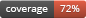
dev-master
9999999-dev https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl ~2.2
- zendframework/zend-mvc ~2.2
- zendframework/zend-eventmanager ~2.2
- zendframework/zend-servicemanager ~2.2
- zendframework/zend-http ~2.2
- zendframework/zend-view ~2.2
- zendframework/zend-cache ~2.2
The Development Requires
- doctrine/common >=2.3,<2.5-dev
- zendframework/zend-developer-tools 0.*
- squizlabs/php_codesniffer 1.4.*
- phpunit/phpunit ~3.7
- satooshi/php-coveralls ~0.6
- zf-commons/zfc-user 1.*
acl zf2 zfc-user
1.5.0-beta1
1.5.0.0-beta1 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl ~2.1
- zendframework/zend-mvc ~2.1
- zendframework/zend-eventmanager ~2.1
- zendframework/zend-servicemanager ~2.1
- zendframework/zend-http ~2.1
- zendframework/zend-view ~2.1
- zendframework/zend-cache ~2.1
The Development Requires
- phpunit/phpunit ~3.7
- doctrine/common >=2.3,<2.5-dev
- zendframework/zend-developer-tools 0.*
- zf-commons/zfc-user 0.*
- squizlabs/php_codesniffer 1.4.*
- satooshi/php-coveralls ~0.6
acl zf2 zfc-user
1.4.0
1.4.0.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl ~2.1
- zendframework/zend-mvc ~2.1
- zendframework/zend-eventmanager ~2.1
- zendframework/zend-servicemanager ~2.1
- zendframework/zend-http ~2.1
- zendframework/zend-view ~2.1
- zendframework/zend-cache ~2.1
The Development Requires
- phpunit/phpunit ~3.7
- doctrine/common >=2.3,<2.5-dev
- zendframework/zend-developer-tools 0.*
- zf-commons/zfc-user 0.*
- squizlabs/php_codesniffer 1.4.*
- satooshi/php-coveralls ~0.6
acl zf2 zfc-user
1.4.0-beta1
1.4.0.0-beta1 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl ~2.1
- zendframework/zend-mvc ~2.1
- zendframework/zend-eventmanager ~2.1
- zendframework/zend-servicemanager ~2.1
- zendframework/zend-http ~2.1
- zendframework/zend-view ~2.1
- zendframework/zend-cache ~2.1
The Development Requires
- doctrine/common >=2.3,<2.5-dev
- zendframework/zend-developer-tools 0.*
- zf-commons/zfc-user 0.*
- squizlabs/php_codesniffer 1.4.*
- phpunit/phpunit ~3.7
- satooshi/php-coveralls ~0.6
acl zf2 zfc-user
1.3.1
1.3.1.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl ~2.1
- zendframework/zend-mvc ~2.1
- zendframework/zend-eventmanager ~2.1
- zendframework/zend-servicemanager ~2.1
- zendframework/zend-http ~2.1
- zendframework/zend-view ~2.1
The Development Requires
- doctrine/common >=2.3,<2.5-dev
- zendframework/zend-developer-tools 0.*
- zf-commons/zfc-user 0.*
- phpunit/phpunit ~3.7
- satooshi/php-coveralls ~0.6
acl zf2 zfc-user
1.3.0
1.3.0.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl ~2.1
- zendframework/zend-mvc ~2.1
- zendframework/zend-eventmanager ~2.1
- zendframework/zend-servicemanager ~2.1
- zendframework/zend-view ~2.1
The Development Requires
- doctrine/common >=2.3,<2.5-dev
- zendframework/zend-developer-tools 0.*
- zf-commons/zfc-user 0.*
- phpunit/phpunit ~3.7
- satooshi/php-coveralls ~0.6
acl zf2 zfc-user
1.2.6
1.2.6.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl ~2.1
- zendframework/zend-mvc ~2.1
- zendframework/zend-eventmanager ~2.1
- zendframework/zend-servicemanager ~2.1
- zendframework/zend-view ~2.1
The Development Requires
acl zf2 zfc-user
1.2.5
1.2.5.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl ~2.1
- zendframework/zend-mvc ~2.1
- zendframework/zend-eventmanager ~2.1
- zendframework/zend-servicemanager ~2.1
- zendframework/zend-view ~2.1
The Development Requires
acl zf2 zfc-user
1.2.4
1.2.4.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl 2.1.*
- zendframework/zend-mvc 2.1.*
- zendframework/zend-eventmanager 2.1.*
- zendframework/zend-servicemanager 2.1.*
- zendframework/zend-view 2.1.*
The Development Requires
acl zf2 zfc-user
1.2.3
1.2.3.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl 2.1.*
- zendframework/zend-mvc 2.1.*
- zendframework/zend-eventmanager 2.1.*
- zendframework/zend-servicemanager 2.1.*
- zendframework/zend-view 2.1.*
The Development Requires
acl zf2 zfc-user
1.2.2
1.2.2.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl 2.1.*
- zendframework/zend-mvc 2.1.*
- zendframework/zend-eventmanager 2.1.*
- zendframework/zend-servicemanager 2.1.*
- zendframework/zend-view 2.1.*
The Development Requires
acl zf2 zfc-user
1.2.1
1.2.1.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl 2.1.*
- zendframework/zend-mvc 2.1.*
- zendframework/zend-eventmanager 2.1.*
- zendframework/zend-servicemanager 2.1.*
- zendframework/zend-view 2.1.*
The Development Requires
acl zf2 zfc-user
1.2.0
1.2.0.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl 2.1.*
- zendframework/zend-mvc 2.1.*
- zendframework/zend-eventmanager 2.1.*
- zendframework/zend-servicemanager 2.1.*
- zendframework/zend-view 2.1.*
The Development Requires
acl zf2 zfc-user
1.1.2
1.1.2.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl 2.*
- zendframework/zend-mvc 2.*
- zendframework/zend-eventmanager 2.*
- zendframework/zend-servicemanager 2.*
- zendframework/zend-view 2.*
- zf-commons/zfc-base ~0.1
- zf-commons/zfc-user ~0.1
The Development Requires
acl zf2 zfc-user
1.1.1
1.1.1.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zend-permissions-acl 2.*
- zendframework/zend-mvc 2.*
- zendframework/zend-eventmanager 2.*
- zendframework/zend-servicemanager 2.*
- zendframework/zend-view 2.*
- zf-commons/zfc-base ~0.1
- zf-commons/zfc-user ~0.1
The Development Requires
acl zf2 zfc-user
1.1.0
1.1.0.0 https://github.com/bjyoungblood/BjyAuthorizeZend\Acl based firewall system for ZF2 dispatch protection
BSD-3-Clause
The Requires
- php >=5.3.3
- zendframework/zendframework 2.*
- zf-commons/zfc-base dev-master
- zf-commons/zfc-user dev-master
The Development Requires
acl zf2 zfc-user
1.0.0
1.0.0.0 https://github.com/bjyoungblood/BjyAuthorizeEasy-use loader and manager for Zend\Acl with built-in route and dispatch protection
The Requires
- php >=5.3.3
- zendframework/zendframework 2.*
- zf-commons/zfc-base dev-master
- zf-commons/zfc-user dev-master
acl zf2 zfc-user
 Wallogit.com
Wallogit.com