dev-master
9999999-devJWT Authentication for WPGraphQL
GPLv3 GPL-3.0+
The Requires
The Development Requires
by
 jasonbahl
jasonbahl
0.3.1
0.3.1.0JWT Authentication for WPGraphQL
GPL-3.0+
The Requires
The Development Requires
by
 jasonbahl
jasonbahl
dev-bug/#17-viewer-query-not-returning-authenticated-user
dev-bug/#17-viewer-query-not-returning-authenticated-userJWT Authentication for WPGraphQL
GPL-3.0+
The Requires
The Development Requires
by
 jasonbahl
jasonbahl
dev-feature/update-gpl-identifier
dev-feature/update-gpl-identifierJWT Authentication for WPGraphQL
GPL-3.0+
The Requires
The Development Requires
by
 jasonbahl
jasonbahl
dev-bug/#13-tokens-are-identical
dev-bug/#13-tokens-are-identicalJWT Authentication for WPGraphQL
GPLv3
The Requires
The Development Requires
by
 jasonbahl
jasonbahl
0.2.1
0.2.1.0JWT Authentication for WPGraphQL
The Requires
The Development Requires
by
 jasonbahl
jasonbahl
 Wallogit.com
Wallogit.com
 , (*1)
, (*1)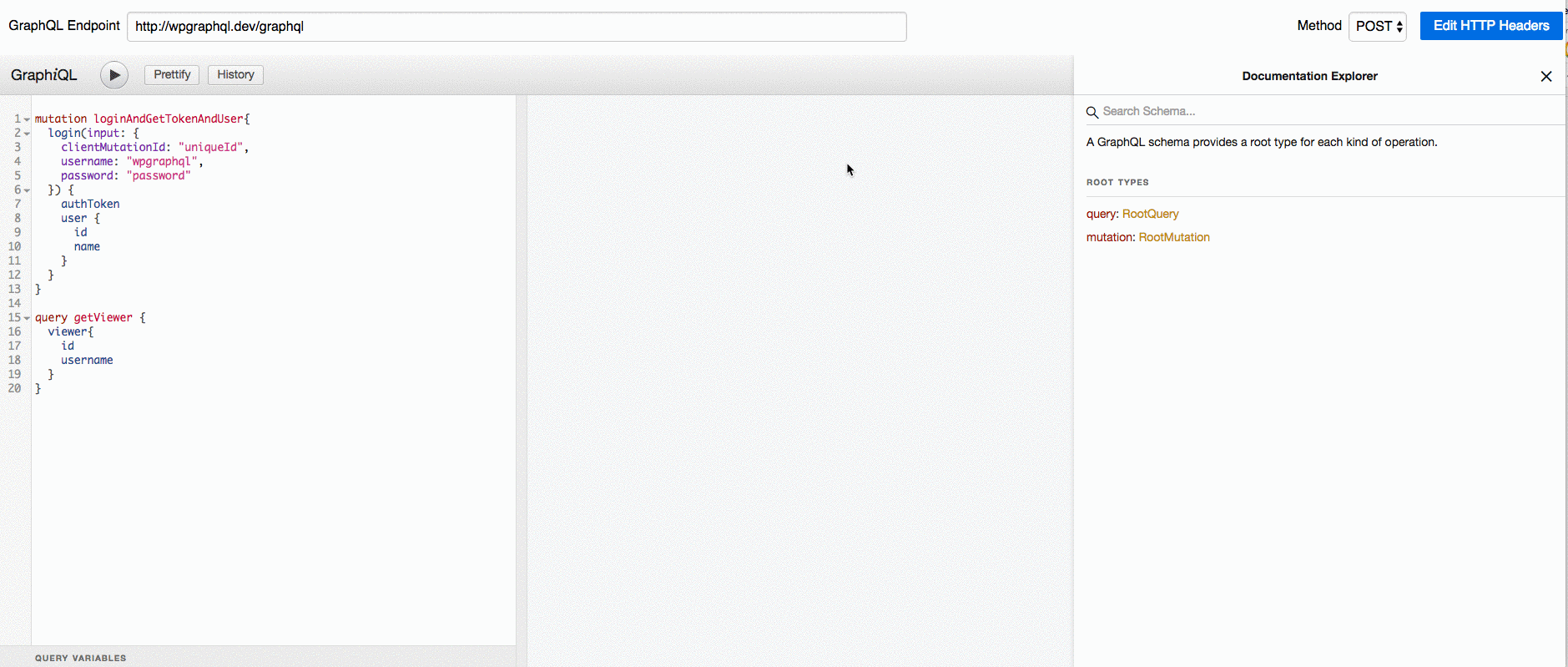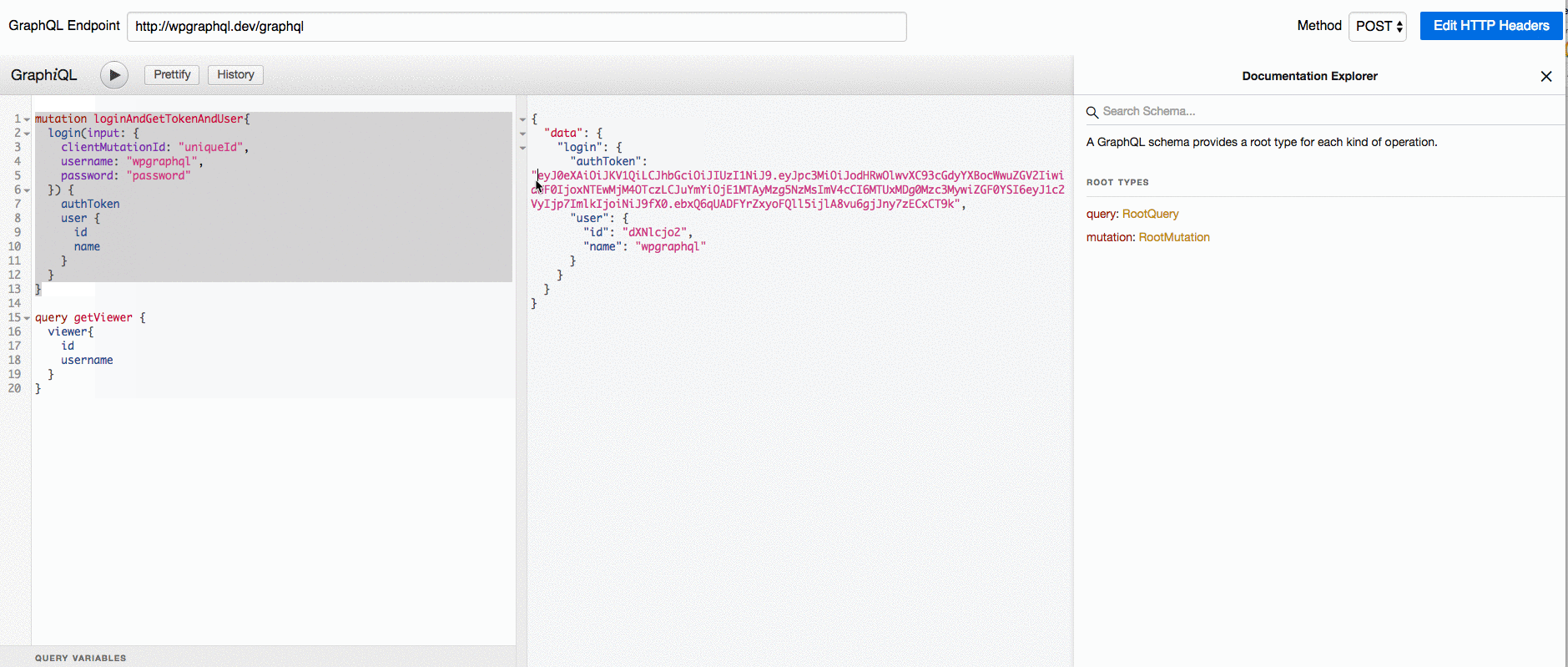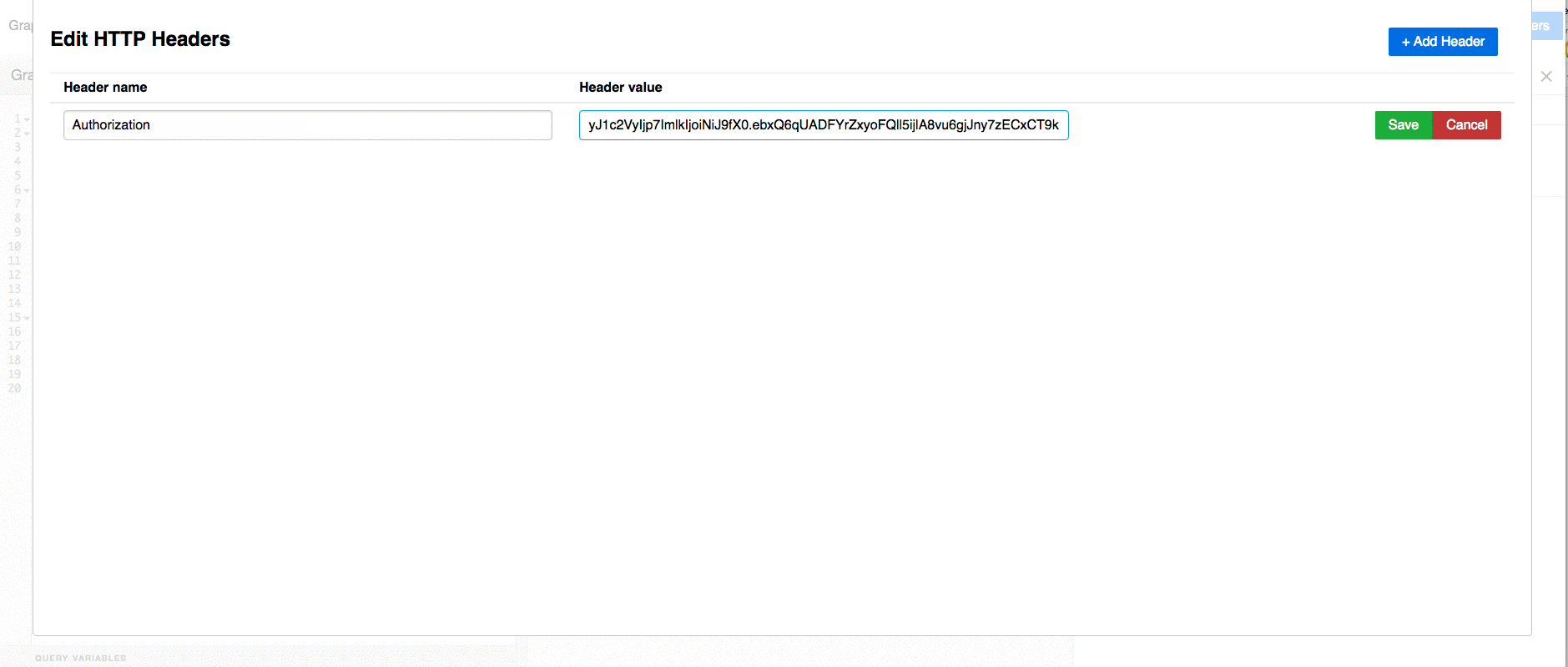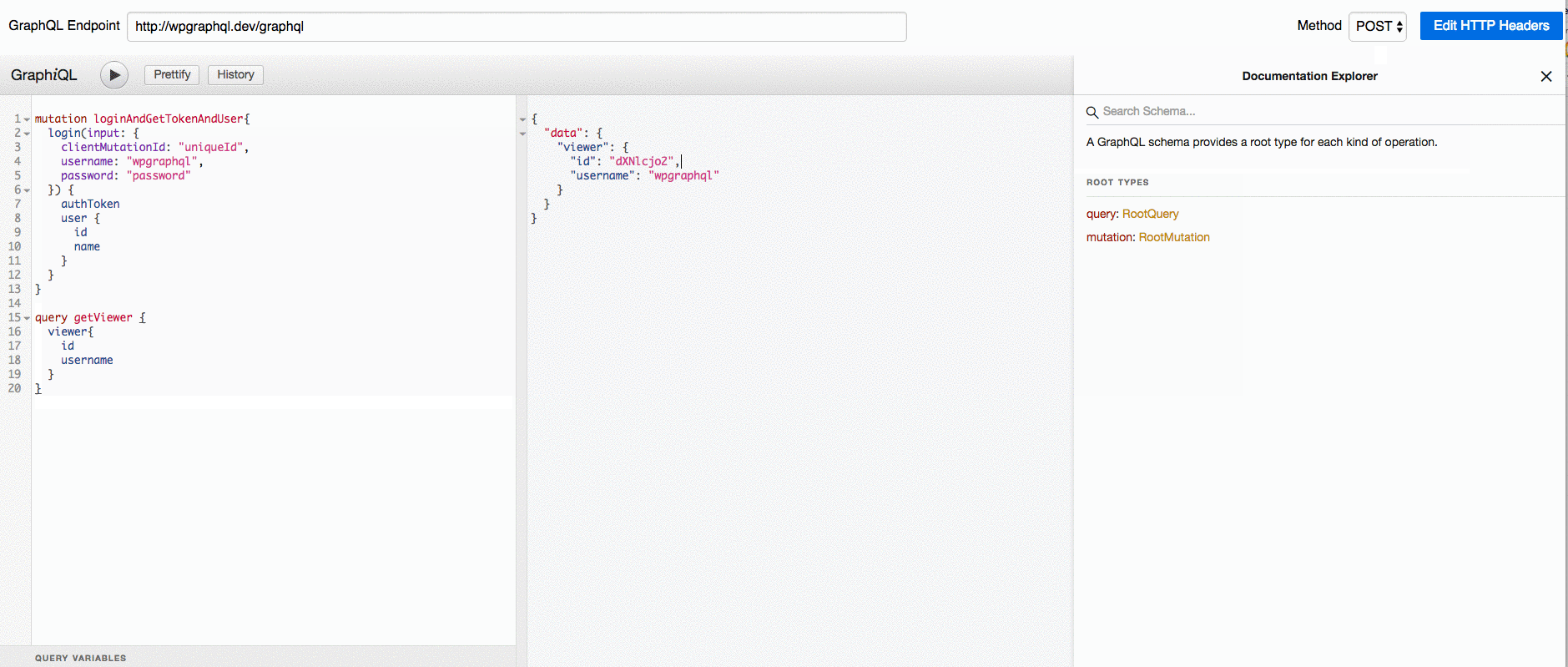 , (*23)
, (*23)